
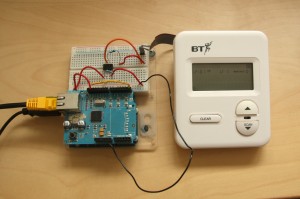
The project uses a BT Caller Display 50 connected via an optoisolating bridge to an Arduino with an ethernet shield. When an incoming call is received, the telephone number is transmitted via MQTT to a python client on any computer. This project is a great example of someone putting great effort into being lazy, the caller id data is already displayed on my phone but the phone generally resides in the next room so this avoids me needing to run for stupid cold callers. Initially I’d wanted to do this project just using the Arduino, which may have been possible but using the CD50 makes it a huge amount easier.
Hardware
The hardware is very simple as the CD50 has an internal serial port so all that’s required is to safely isolate the phone line from any sensitive computer systems with an optoisolator.
CD50
The CD50 has been hacked to provide serial output in a couple of projects before. However, all the pages documenting this have long gone (the unit is around 10yrs old). Internally the unit uses two EXAR XR-2211 FSK Demodulator/ Tone Decoders, one to detect the presence of the signal and one to decode it (allegedly). In this configuration this means serial data is outputted on pin 7 of the left chip (see below)

Bridge
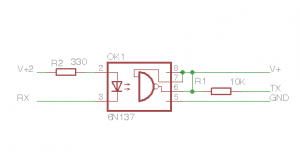
The optoisolating bridge protects connected equipment from high voltages which can occur in telephone lines, here I used the Vishay 6N137 device as shown (I chose the Vishay as it requires very low current). I powered the CD50 side using the power supply on pin 1 and the arduino side using the internal power supply from the arduino. The 6N137 was sourced from Farnell.
Arduino
The Arduino simply receives the serial data using its hardware serial port (I had mixed results with a software serial port), parses the telephone number from the output and then sends it in an MQTT message it would be simple to pass it using over usb back to the computer if you are not using MQTT too.
Source and original link = http://oliversmith.io/technology/2011/10/02/mqtt-caller-display-hacking-the-bt-caller-display-50-serial-port/

COMMENTS